Over the past few months, I have been regularly getting ‘Is that you in the video‘ malware messages on my Facebook inbox. Though I never clicked any of such, many of my friends have become the victim of such malware.
With technologies advancing at a very fast pace, hackers and scammers are finding more and more creative ways to attack and hack people’s accounts.
A few months ago I blog about the new phishing technique ‘Browser In The Browser’ (BIBT) and how many of us can easily fall for such a simple yet effective phishing technique.
Yesterday I stumbled upon a YouTube video by NetworkChuck where he talks about the BeEF program and how one can easily hack the browser using the BeEF tool.
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser. Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser. BeEF will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.
I had to check it out and test the tool. So I got myself a Linode account as its the easiest way to install BeEF.
Installing BeEF on linode was pretty easy. Watch this video to learn how to install BeEF on linode.
Here’s the step to install BeEF in linode.
1. First head over to linode.com and create your account. Ps.. this is not an affiliate link.
2. From the Create section, choose Linode
3. From the Marketplace, Choose BeEF
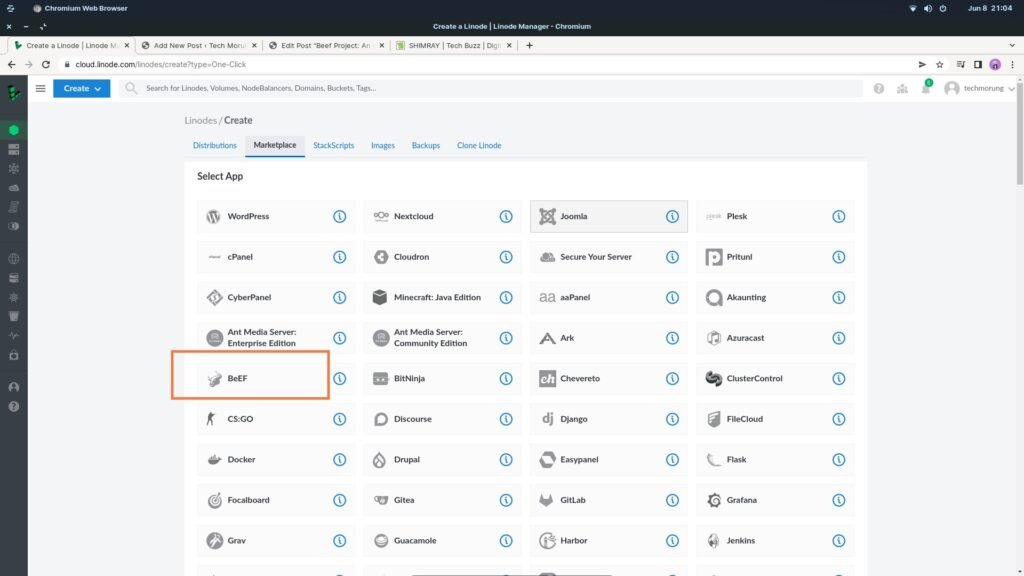
4. Under BeEF options, provide BeEF password and email address. This password will be used to login to your BeEF admin panel.
5. Scroll down and select your Region and server Plan. In my demo I had chosen Mumbai as my server location and Shared CPU Nanode 1 GB Plan
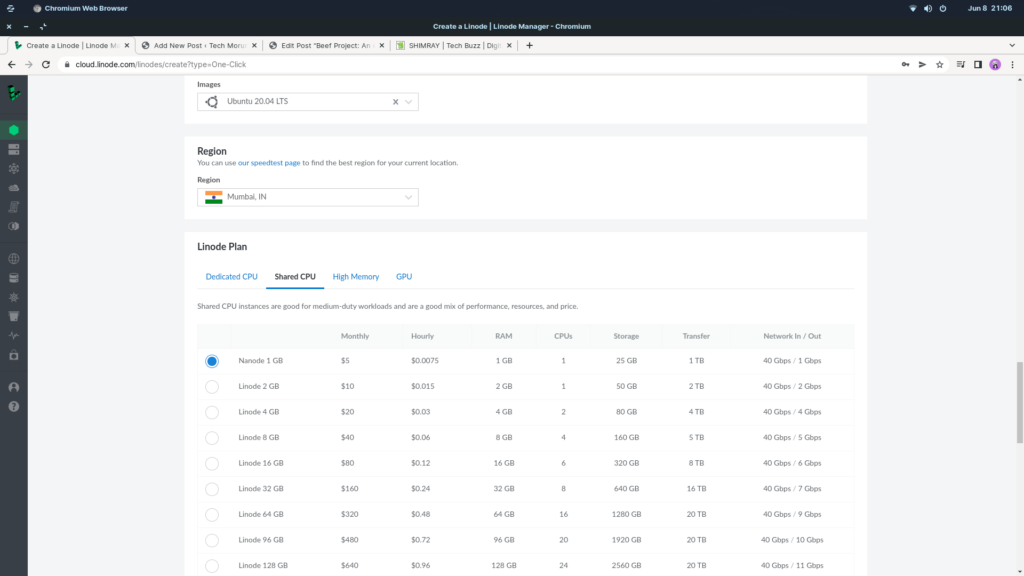
6. Scroll down further and create your Root Password.
7. Click Create Linode.
8. Your Linode will boot. Wait for it to Start Running. Once it starts Running, copy the SSH Access
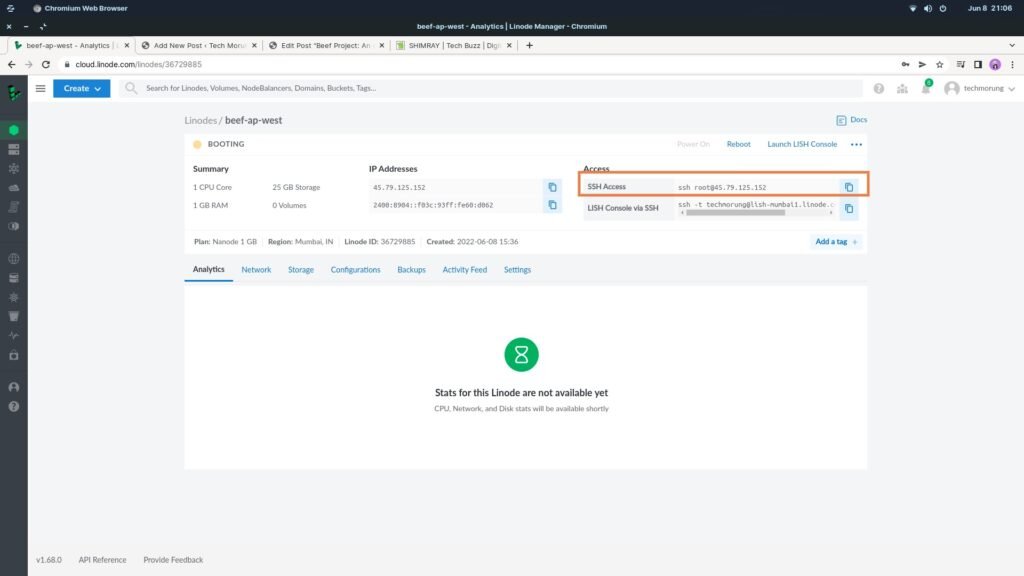
9. Now open your Command Prompt, if you are using Windows, or your Terminal if you are using Linux. In my case, I’m on Zorin OS, which is a Linux-based OS.
10. In your terminal/command prompt, paste your SSH Access from the Linode.
11. Type cat /root/beef.info. If it shows Folder not found, give it some time.
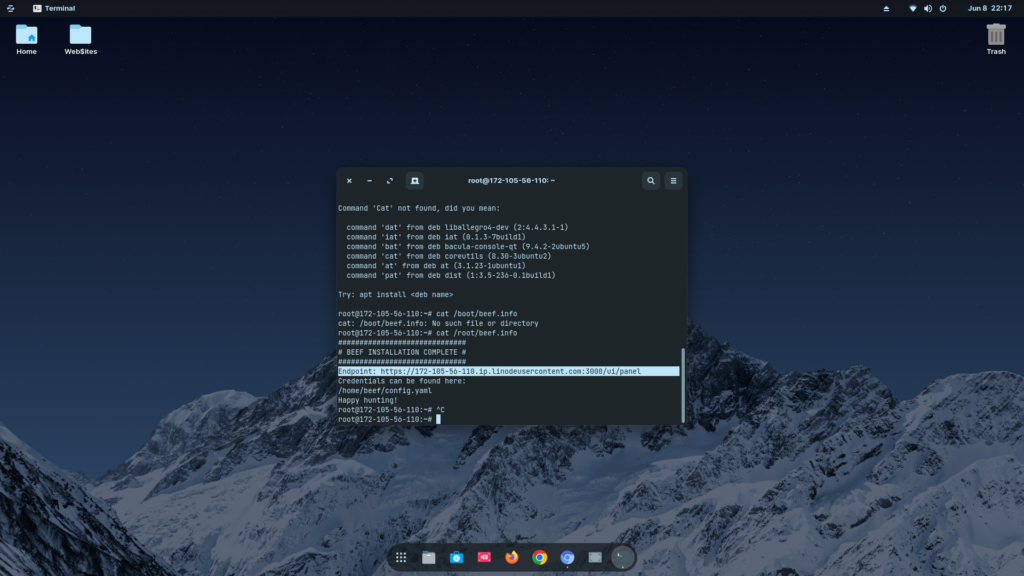
12. Once you run cat /root/beef.info, you will get the link to your BeEF panel. Copy the link and open it in your browser.
13. Login to your BeEF admin panel. And copy the advanced link. With some codings, you will be able to change the web page of the advanced link. This link is your target link.
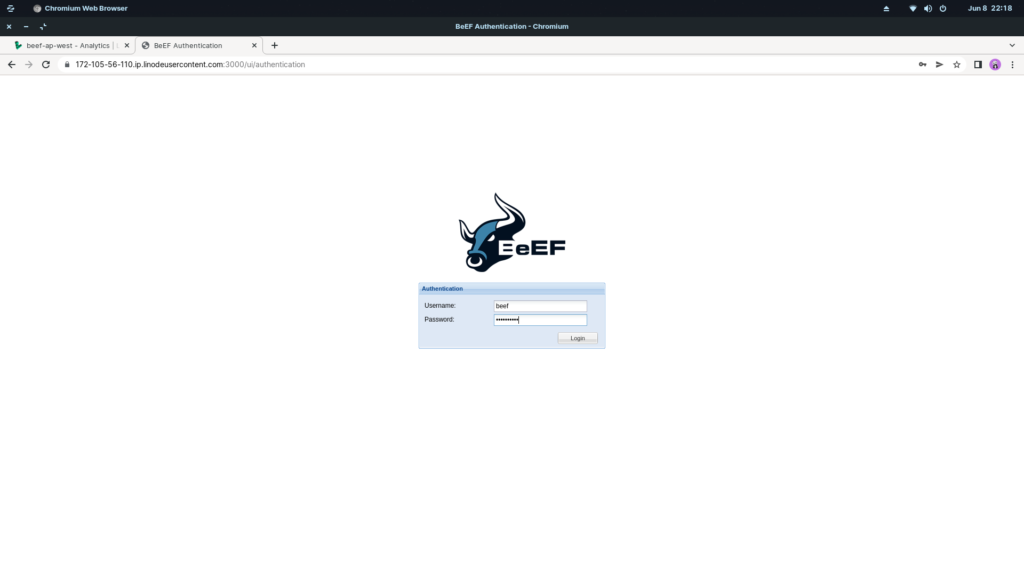
14. Copy the link and send it to your target. Once your target opens the link, their browser gets hooked. And you will be able to execute many of the hacking and phishing programs from the BeEF panel.
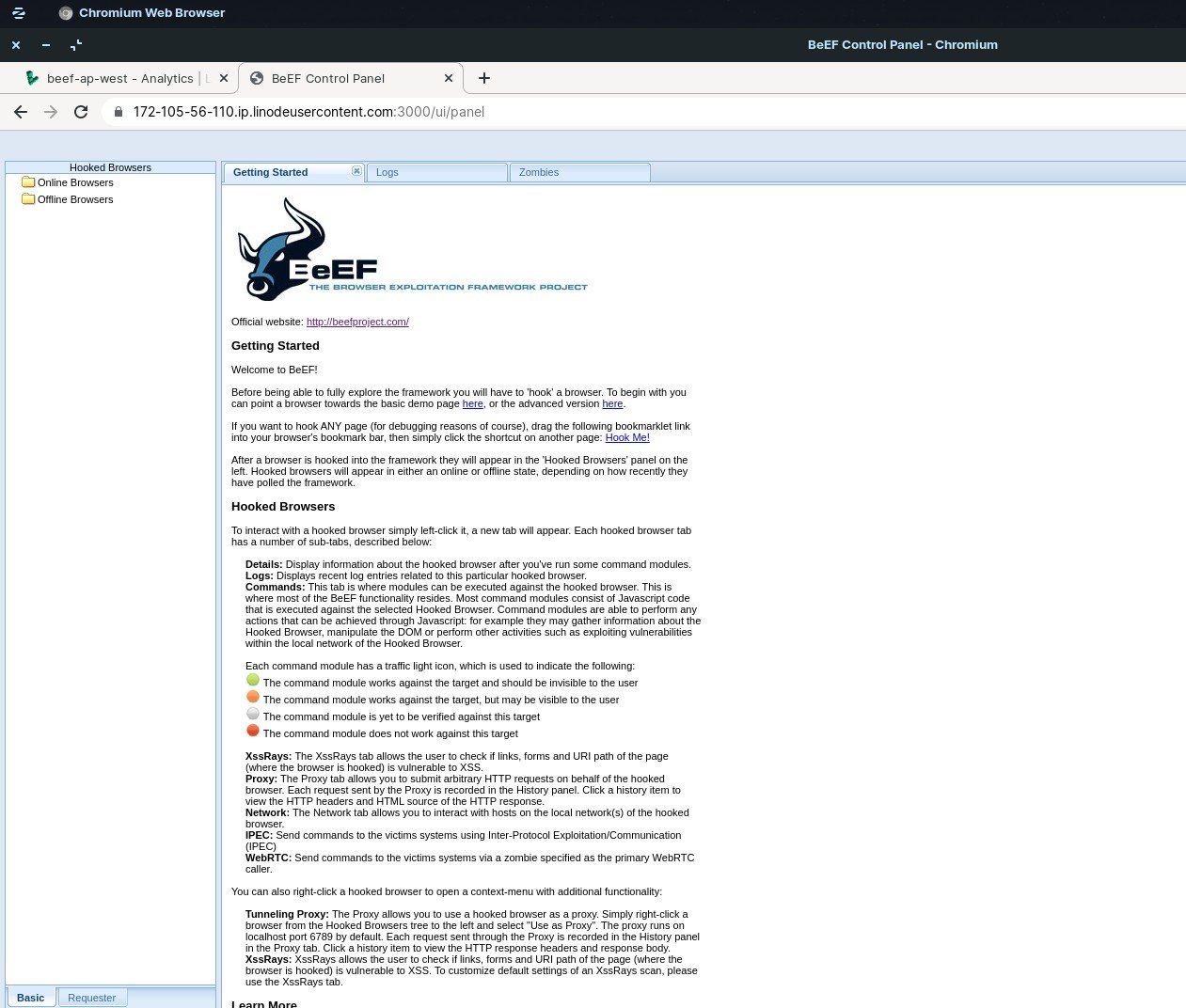
Executing BeEF Hacking Tool
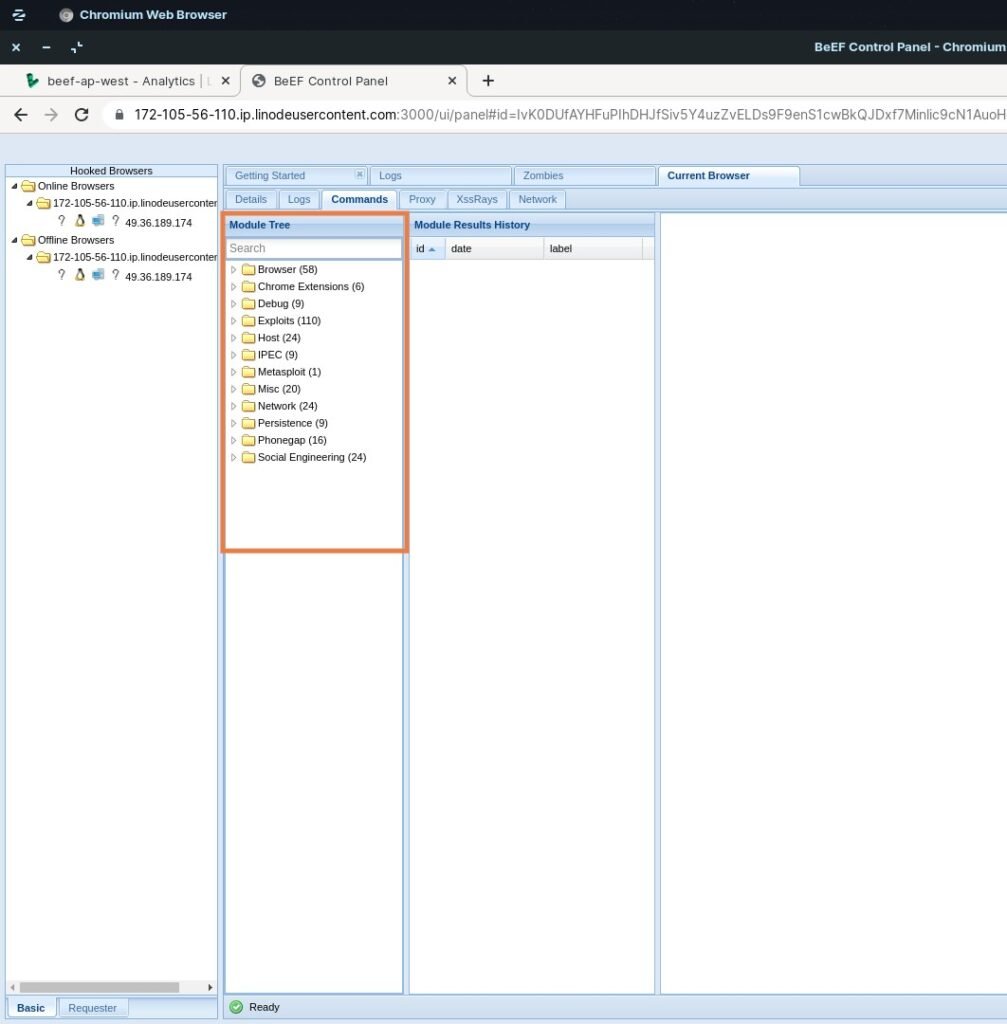
Executing the program is easy and is just a click away. Once you have sent the link to your target and once it’s hooked, you can execute many programs which have been clubbed together under various categories as seen in the picture below.
Watch this video to see how to execute the program from BeEF admin panel.
Among the many programs, my favourites are from the Social Engineering category where I can execute phishing programs to get the credentials of Gmail, Facebook etc.
To execute Google phishing, just visit the Social Engineering category and locate Google Phishing and click execute. Your target and hooked browser will see the Gmail login page. Once they put in their credentials, it will take them to an Unable to Connect page and also another tab with the actual login page of Gmail.
However, if they have put in their credentials, you will be able to see their username and password from the command results.
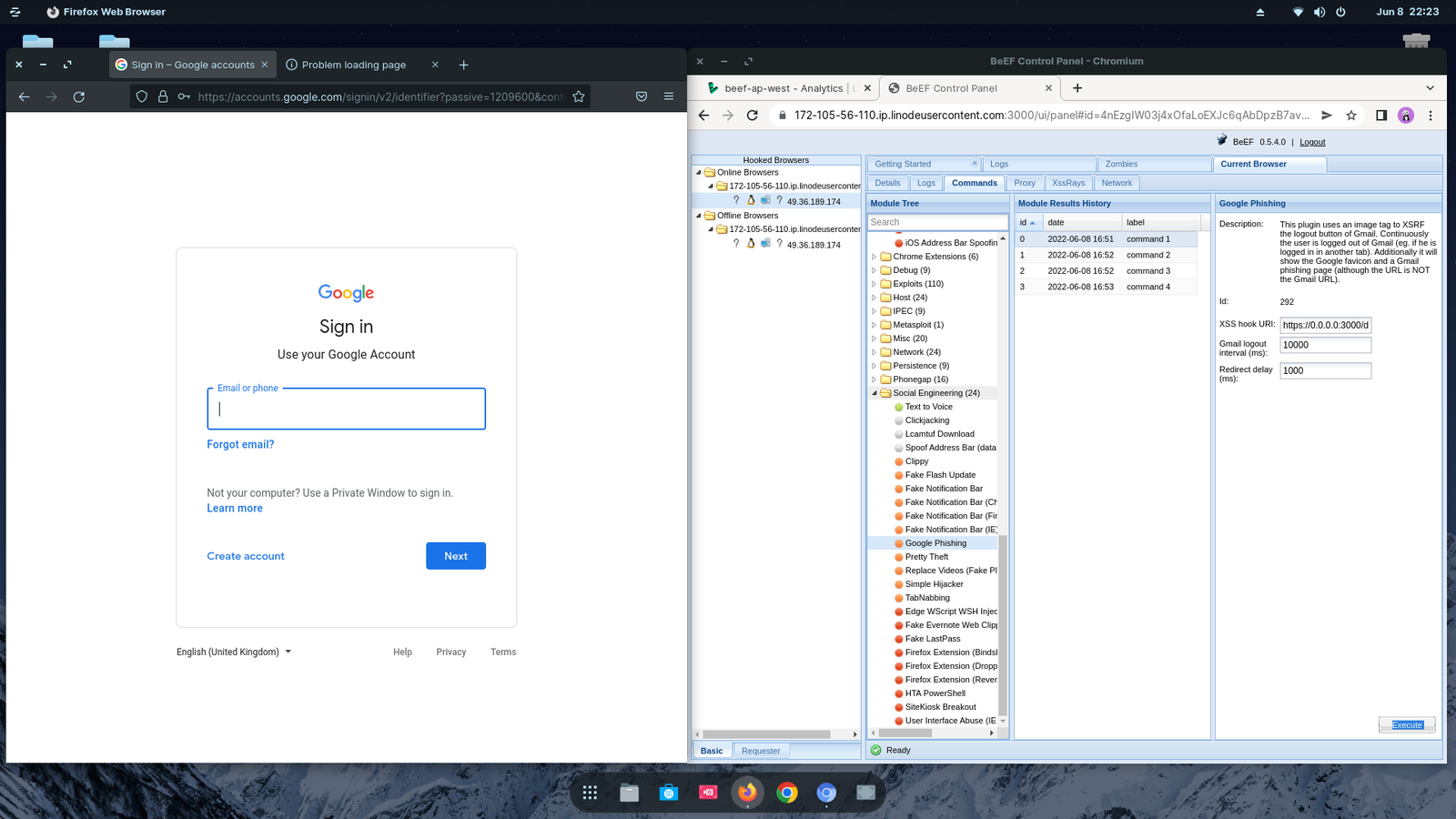
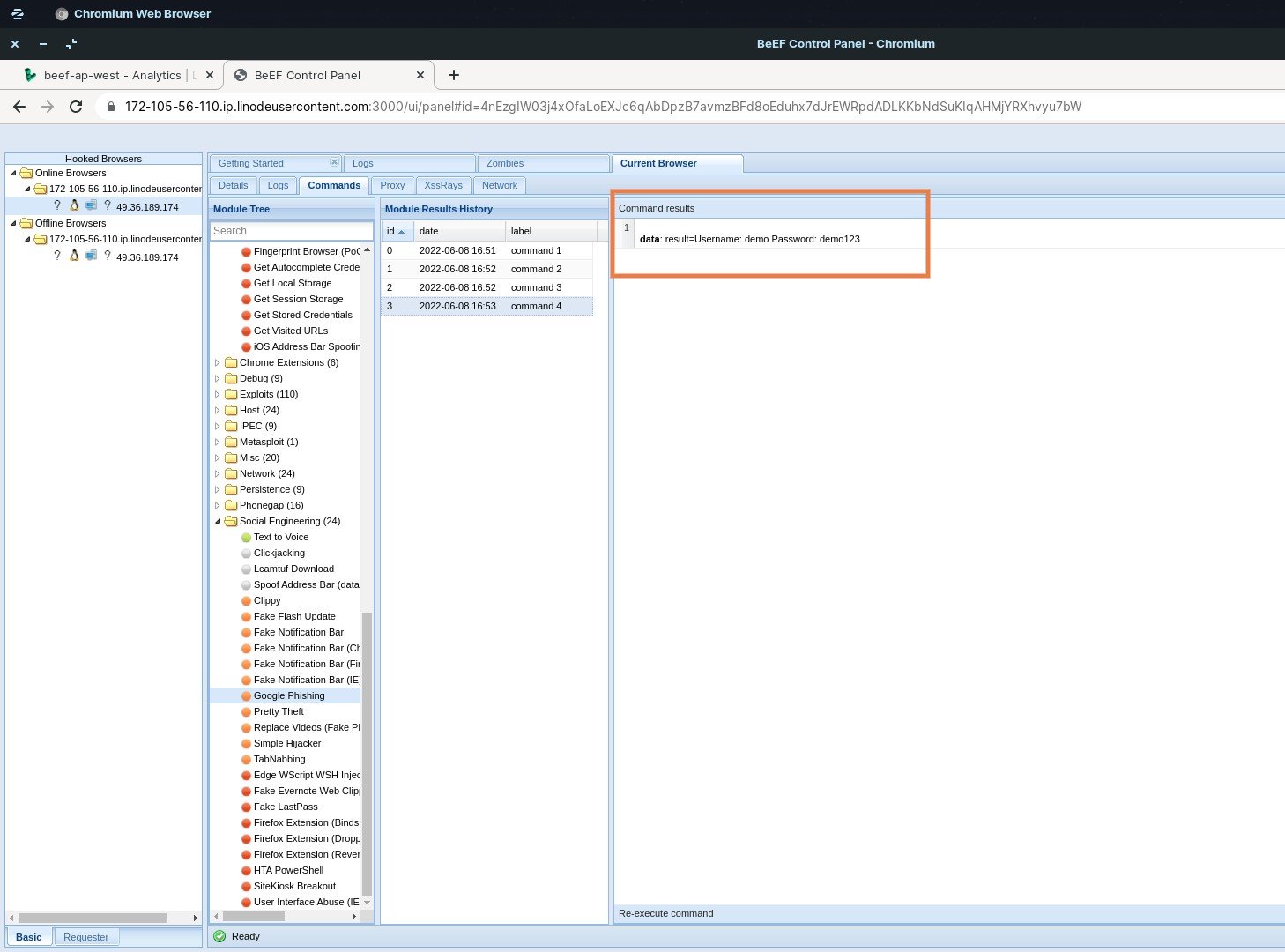
The BeEF program leaves ample opportunities for hackers to hack your system or steal your credentials. With a little bit of coding and creativity, they will be able to hack your system or steal your credentials.
This blog post is for educational purposes only. Please stay away from hacking and stay safe from hackers. Don’t click on unnecessary or suspicious links. Be more cautious when you sign up for websites that guarantee you free expensive gifts








